|
| Link: Link
Downloads: 17747
| Submitted: Jan 12 2004
Updated: Jan 31 2008
| |
Description:
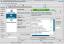
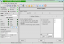
KMyFirewall attempts to make it easier to setup IPTables based firewalls on Linux systems.
It will be the right tool if you like to have a so called "Personal Firewall" running on your Linux box, but don't have the time and/or the interest to spend hours in front of the IPTables manual just to setup a Firewall that keeps the "bad" people out.
Changelog:
Hi,
Donatas Glodenis provides KMyFirewall 1.1.1 and patched kdesudo packages for Ubuntu/Kubuntu at http://dg.lapas.info/share/paketai/ubuntu-gutsy/
thanks for his support!
greetz,
chris
---
Hi,
As reported by Donatas Gloden the installation process in version 1.1.0 is seriously broken - IT DOES NOT INSTALL A VALID SCRIPT!
So please Update to v1.1.1 that i've just released on sf.net if you are using 1.1.0!
---
Hi,
With great thanks to Donatas Glodenis here is a much better fix solving the "kdesu -t issue". Here are the instructions form his email:
The kdesudo version 2.1, available for the coming version of Ubuntu Hardy
Heron (8.4), already has the -t option implemented. You can build your own
kdesudo package for gutsy by following these steps:
1. Download these packages from the repositories:
$ wget http://archive.ubuntu.com/ubuntu/pool/main/k/kdesudo/kdesudo_2.1-0ubuntu1.dsc
$ wget
http://archive.ubuntu.com/ubuntu/pool/main/k/kdesudo/kdesudo_2.1.orig.tar.gz
$ wget
http://archive.ubuntu.com/ubuntu/pool/main/k/kdesudo/kdesudo_2.1-0ubuntu1.diff.gz
2. setup sources:
$ dpkg-source -x kdesudo_2.1-0ubuntu1.dsc
3. Build package:
$ cd kdesudo-2.1/
$ sudo apt-get build-dep kdesudo
$ dpkg-buildpackage -rfakeroot -uc -b
4. Install package
$ cd ../
$ sudo dpkg -i kdesudo*.deb
Here is the apt-get source for KMyFirewall and the patched KDEsudo
http://dg.lapas.info/share/paketai/ubuntu-gutsy/
greetings,
chris
---
Release of KMyFirewall 1.1.0
Well, it has been a while since the last release, almost 2 years ;)
Sorry for the slow progress until now, but i hope the new KMyFirewall 1.1.0 release will excuse the long waiting.
This release includes lots of cool new features (e.g. multi target configuration, remote installation etc.) and fixes all known bugs. Again the document format has changed a bit but i did my best to make it compatible with rule sets created using v1.0.x
Multi Target Configuration & Remote firewall control
With KMyFirewall 1.1.0 you are now able to define so called Targets (accessible in the MyNetwork View), those are the computers you like to manage using KMyFirewall.
After configuring a target (IP address and SSH port) you simply set it as the "Active Target" and edit it's rule set as you did for localhost. The only requirement is that the target allows SSH connections and has a bash shell installed.
With the help of KDE's KIO technology you can install, run, show configuration etc. on the remote host, as you did on localhost before.
All communication between KMyFirewall and the target is encrypted using SSH.
New Undo/Redo Engine
As consequence to the lots of trouble the current undo/redo implementation has made, i re-designed it and as result the engine is faster, more reliable and much easier to use as a developer.
Custom Protocols (Generic Interface)
This solves on of the most annoying problems of the Generic Interface. In KMyFirewall's settings dialog you now can define your own protocols.
So if you find any important protocol still missing, simply create it and if you like send it to chubinger_AT_irrsinnig_DOT_org so that i can add it for the next release. (For the future i plan to implement a KHotNewStuff service to allow online updates of the protocol library.)
Improved Auto Configuration
The auto configuration capabilities have been moved to a small bash script and therefore can also be used for remote targets. If your system is not detected correctly please send your configuration to chubinger_AT_irrsinnig_DOT_org so that i can add them to the auto configuration script.
So finally i just like to say have fun managing your firewalls using KMyFirewall 1.1.0
Feedback and burg reports are very welcome.
greetings,
Chris
----
Release of KMyFirewall 1.0.1
* Adding some more protocols to the Protocol library
* Fix spelling bug in Workstation template
* Small code cleanup
* Deleted old Parser and Wizrad files
* Fix rule index handling
* Allow insert of rules.
* Fix Rule renamed canceled bug
* cleanup interface add parameter to select the config part to show insted of different methods
* Add posibilty to export a package containing the scripts needed to install the ruleset on the system
* Add commandline parameter to define the GUI interface to startup with
* Fix chain log prefix saving bug
* Fix multiport ruleoption bug
-----
Release of KMyFirewall 1.0
Important: As the file format used to save the rulesets has changed, rulesets created with KMyFirewall < 1.0beta1 WILL NOT work, don't even try it!
Since the last stable release KMF has been completely rewritten in order to be even more flexible and on the other hand easier to use.
New plugin framework
Most parts of the application has been rewritten introducing a plugin framework that allows to add new IPTables rule option editors to be written within a few hours (well maybe days depends on the options complexity :).
This will allow us (and contributors) to easily implement the fast growing number of IPTables ruleoptions without the need of understanding the whole application.
The backend generating the IPTables rules itself has been extended to allow the registration of new rule options by defining them in an XML description file. For a detailed description about how to write such plugins have a look at the application handbook in the current CVS version.
So feel free to contribute plugins, there are lots of options still not implemented.
New Easy-To-Use platform independent interface
As I often got mails complaining about the to complex nature of KMF and the very limited possibilities the wizard provides i simply removed the wizard and implemented a completely new interface.
Features of the new Interface
As the new interface works on an abstract descrioption of the generated rules the new plugin structure allows us top implement script compilers that support other firewalling backends than just netfilter/iptables.
To support a new tool kit it is required to write a compiler and an installer plugin for the new framework. Currently just the iptables/linux compiler and installer is implemented. As with the rule option plugins of the IPTables interface it shouldn't bee too much work to develop those plugins.
IPTables vs. Generic interface
The main difference between those two interfaces is that the new Generic Interface is OS and toolkit independant while the IPTables interface is an improved version of the well known KMF GUI and therefore tight bound to the netfiler/iptables toolkit and can therefore only be used with Linux as operating system.
Why two different interfaces?
Especially when concerning security related applications you (as developer) need to decide if you like to build an application used by expert users (e.g. experienced system administrators) or if you like to provide a tool that everybody can handle.
It hasn't been an easy decision to implement one interface for each user group but after pondering about concepts to merge those two requirements into one interface we decided that it is much better to separate them.
This allows us to concentrate on the wishes and wanted features for each of the user groups.
---
Homepage Update
Some developer documentation has been added. Have a look ath the "Documentation" section to see whats new.
---
Uploaded Suse 9.2 rpms.
Thanks to Marcus for contributing those.
APT users may install from the following repository:
ftp://ftp.gwdg.de/pub/linux/suse/apt SuSE/9.2-i386 suser-tux
---
Updating links to www.rockersoft.org Fedora Core 1/2 rpms.
They should also work for FC3
---
Adding debian testing/ustable package contributed by Raphael Lechner
---
New homepage online!
I'm very happy to announce the availability of the new fresh designed KMyFirewall homepage.
The design and implementation was done by Anton Frennevi who also designed a new icon set for KMF.
Unfortuantely he won't have anymore time to work with us so a big thank you very much to him.
---
0.9.6.1 -> 0.9.6.2
Fixed rule creation bug in Wizard
Made adding of other devvice types then the defaults possible
Several small fixes
---
Rockersoft made packages for Fedora Core 1 available via their download server at:
http://www.rockerssoft.com/apt/fedora/1/en/i386/RPMS.rockerssoft/
Those packages are also available via an apt-get repository at:
http://www.rockerssoft.com/apt/fedora/1/en/i386/
Thanks a lot to the guys at Rockerssoft:
http://www.rockerssoft.com/forum/
License: GPL
|
| |
Add commentBack
|